10 Cybersecurity Tools That May Cause a False Sense of Security
By:
Ganesan D
24 Jan 2025
Category:
Cyber security Tools
Many businesses invest in cybersecurity tools believing they
provide complete protection. However, these tools can create gaps
in security if not properly managed. Below, we identify common
cybersecurity tools, why they create a false sense of security,
and how to fix these security weaknesses.
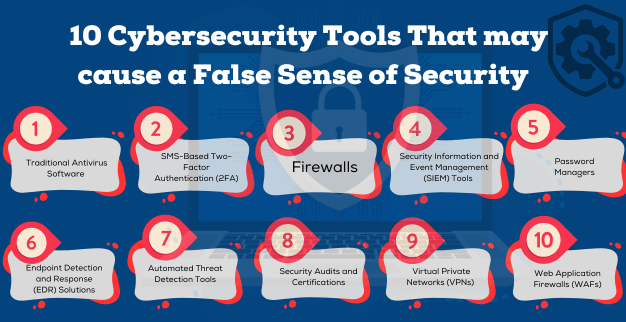
1. Traditional Antivirus Software
Cause: Signature-based antivirus tools like
McAfee, Norton, and Avast only detect known threats and fail to
stop zero-day attacks and fileless malware.
Solution: Upgrade to Next-Generation Antivirus
(NGAV) solutions like CrowdStrike Falcon, SentinelOne, or
Microsoft Defender for Endpoint, which use AI-driven threat
detection and behavioral analysis.
2. SMS-Based Two-Factor Authentication (2FA)
Cause: Hackers can intercept SMS messages through
SIM swapping, phishing, and malware. Many users assume SMS 2FA is
unbreakable, leading to weak security.
Solution: Replace SMS-based 2FA with hardware
security keys (YubiKey, Google Titan) or authenticator apps
(Google Authenticator, Microsoft Authenticator, Duo Security) for
stronger authentication.
3. Firewalls
Cause: Firewalls like Cisco ASA, Fortinet, and
pfSense protect networks but cannot block insider threats, social
engineering attacks, or encrypted malware traffic.
Solution: Use a Zero Trust Security Model (ZTNA)
that continuously verifies user identity and device
trustworthiness instead of relying on perimeter-based security.
4. Security Information and Event Management (SIEM) Tools
Cause: SIEM solutions like Splunk, IBM QRadar,
and Microsoft Sentinel collect security logs, but they generate
too many false alerts, causing security teams to miss real
threats.
Solution: Implement Extended Detection and
Response (XDR) solutions, which provide better threat correlation,
automation, and incident response.
5. Password Managers
Cause: Password managers like LastPass,
1Password, and Bitwarden store passwords securely, but they cannot
prevent phishing attacks or credential stuffing if users fall for
scams.
Solution: Adopt passwordless authentication
(FIDO2, passkeys, biometrics) and educate users about phishing
awareness.
6. Endpoint Detection and Response (EDR) Solutions
Cause: EDR tools like SentinelOne, CrowdStrike
Falcon, and Microsoft Defender for Endpoint monitor and respond to
endpoint threats but require manual investigation, which can delay
response times.
Solution: Integrate automated threat hunting,
behavior analytics, and AI-driven response mechanisms to detect
threats faster.
7. Automated Threat Detection Tools
Cause: AI-driven tools like Darktrace, Vectra AI,
and Cylance can miss advanced persistent threats (APTs) and
generate false positives, leading to alert fatigue.
Solution: Combine AI-driven security with human
threat intelligence and conduct manual threat-hunting exercises.
8. Security Audits and Certifications
Cause: Many businesses assume that achieving ISO
27001, SOC 2, or PCI DSS certification guarantees complete
security, but compliance does not prevent cyberattacks.
Solution: Conduct regular penetration testing,
red team exercises, and continuous security assessments beyond
compliance requirements.
9. Virtual Private Networks (VPNs)
Cause: VPNs like NordVPN, ExpressVPN, and Cisco
AnyConnect encrypt traffic but cannot protect against malware,
phishing, or stolen credentials.
Solution: Implement Zero Trust Network Access
(ZTNA) and multi-factor authentication (MFA) for secure remote
access.
10. Web Application Firewalls (WAFs)
Cause: WAFs like Cloudflare, AWS WAF, and Imperva
protect against common attacks but cannot stop business logic
flaws, API vulnerabilities, or supply chain attacks.
Solution: Perform regular penetration testing,
API security assessments, and continuous security monitoring to
detect vulnerabilities beyond WAF protection.
Relying solely on cybersecurity tools without continuous
monitoring, proactive threat detection, and expert intervention
can expose your business to cyber threats. At Agan Cyber Security
LLC, we provide customized security solutions, including
penetration testing, risk assessments, and real-time threat
intelligence to protect your business.