Clicks and Consequences: How Digital Marketing Opens Doors for Cyber Threats
Cybersecurity acts as a barrier against potential threats, protecting a digital marketing environment driven by technology and the internet.
Read More
Cybersecurity acts as a barrier against potential threats, protecting a digital marketing environment driven by technology and the internet.
Read More
Zero Trust security is an IT security model that requires strict identity verification for every person and device trying to access resources on a private network, regardless of whether they are sitting within or outside of the network perimeter.
Read More
Traditional technologies may still power your systems—but hidden vulnerabilities in outdated software can expose your website to serious cyber threats.
Read More
A pick-proof lock is a specialized door lock that claims to withstand lock picking, bumping, and other malicious lock manipulation techniques. A pick-proof lock has special security features that make lock picking extremely difficult.
Read More
Cybersecurity, also known as information technology security, is the practice of protecting systems, networks, and programs from digital attacks, damage, or unauthorized access.
Read More
Continuous compliance refers to the ongoing process of monitoring, enforcing, and validating that security controls meet regulatory and internal policy standards at all times — not just during audits.
Read More
As the digital landscape evolves, autopilot technologies—whether in vehicles, business processes, or software—are becoming more advanced, intelligent, and integrated.
Read More
As threats become more sophisticated and real-time responses more critical, organizations are turning to automation to protect digital assets, reduce human error, and stay ahead of cybercriminals.
Read More
In today’s competitive digital landscape, sales and marketing teams rely heavily on Customer Relationship Management (CRM) systems to manage leads, track interactions, and drive conversions
Read More
Autopilot automation handles repetitive, rule-based tasks without human intervention, significantly reducing the time spent on manual operations like data entry, document creation, and email follow-ups.
Read More
As technology evolves, IT departments face increasing pressure to do more with less—faster, safer, and smarter. In 2025, automation is no longer just a competitive edge; it's a necessity.
Read More
Discover how UiPath bots automate HR tasks like onboarding, recruitment, payroll, and employee data—reducing manual effort and increasing accuracy across workflows.
Read More
Discover how UiPath bots automate HR tasks like onboarding, recruitment, payroll, and employee data—reducing manual effort and increasing accuracy across workflows.
Read More
Automation handles repetitive, time-consuming tasks like log analysis or patch management, but human expertise is essential for threat hunting, interpreting context, and making strategic decisions.
Read More
In the UAE, it's a growing focus across sectors due to the country's rapid digital transformation goals aligned with UAE Vision 2031 and smart city initiatives.
Read More
In this article, we’ll explore five actionable tips to improve your automations, ensuring they are not only effective but also scalable, secure, and aligned with your business goals
Read More
These are the 5 common mistakes to avoid during automations to ensure efficiency, accuracy, and long-term success.
Read More
Automating HR processes can significantly boost efficiency, reduce errors, and free up HR teams to focus on strategic tasks. Here’s a clear step-by-step guide to help you get started:
Read More
Penetration testing (pen testing) is a simulated cyberattack by ethical hackers to find and fix security weaknesses in your systems, networks, or applications.
Read More
A well-structured checklist helps ensure security is integrated from the start, covering key areas like access control, firewalls, encryption, and compliance.
Read More
ISO/IEC 27001 is an international standard for managing information security. It shows that an organization has identified risks, assessed their impact, and implemented controls to protect its data.
Read More
Cybersecurity and ERP (Enterprise Resource Planning) security are closely interconnected components of an organization's broader risk management and IT governance strategy.
Read More
ERP Data Breach Prevention: Tips for Secure Implementation is a significant step for any organization, but it also introduces risks, especially around data security.
Read More
Role-Based Access Control (RBAC) is a fundamental security mechanism in Enterprise Resource Planning (ERP) systems, and its importance cannot be overstated.
Read More
To strengthen SAP and Oracle ERP security in 2025, adopt a proactive, multi-layered approach addressing evolving cyber threats, cloud adoption, and AI integration.
Read More
Find genuine HP spare parts in Dubai and the Middle East from trusted authorized distributors for all your replacement needs.
Read More
ERP systems are prime cyberattack targets; learn how to safeguard your critical business data effectively.
Read More
In today’s fast-evolving threat landscape, safeguarding your business requires more than just a strong password or a locked door.
Read More
Securing Windows or Linux servers is essential to protect data and maintain business continuity.
Read More
As the modern workforce continues to embrace remote and hybrid work models, the importance of robust endpoint security has never been more critical.
Read More
Protecting your IT infrastructure is crucial against both internal and external threats.
Read More
Train employees with interactive methods and regular checks to build a strong cybersecurity culture.
Read More
A strong cybersecurity policy protects your business from threats, ensures compliance, and guides employees on safe digital practices.
Read More
Ransomware is a type of malicious software (malware) that encrypts a victim's files or locks their device and demands a ransom in exchange for the decryption key or unlock code.
Read More
In 2025, cybersecurity threats are growing more complex as cybercriminals use AI, automation, and new tactics to exploit weaknesses.
Read More
Small businesses in Dubai and the UAE face unique challenges in maintaining cybersecurity, especially with the increasing frequency and sophistication of cyber threats.
Read More
Traditional security isn’t enough—Dubai businesses are adopting Zero Trust Architecture to better protect against modern cyber threats.
Read More
Enterprise Resource Planning (ERP) systems are the backbone of modern business operations, but they also present several security challenges.
Read More
The integration of Artificial Intelligence (AI) in cybersecurity has transformed the way businesses protect digital assets.
Read More
Cybersecurity is now essential for Dubai businesses as evolving threats demand advanced protection and proactive defense strategies.
Read More
Safeguard your business with Ekran System in Dubai—monitor user activity and control access to prevent insider threats.
Read More
Find reliable HP servers in Dubai with Agan — latest models, UAE warranty, fast delivery, and expert support for your business.
Read More
Explore the latest 2025 Apple MacBooks, iMacs, and accessories in Dubai — shop genuine products from trusted sellers.
Read More
A strong online presence with a well-optimized website is essential for business success in Dubai’s competitive market.
Read More
Dubai businesses face increasing threats like phishing and ransomware, making strong cybersecurity essential.
Read More
Phishing attacks are now among the top cyber threats, using fake emails and websites to trick employees and steal business data.
Read More
Small Dubai businesses face high cyber risks due to limited resources and digital dependence.
Read More
SMEs in the UAE increasingly face pressure to protect both their digital and physical environments in today’s evolving threat landscape.
Read More
In today’s digital age, UAE businesses face growing cyber and physical risks, making strong security essential to prevent major losses.
Read More
With rising cyberattacks and quick physical breaches, picking the right security provider is vital for every business.
Read More
Cybersecurity and physical security are now closely linked, forming one unified approach to business protection.
Read More
Free security audit checklist to help SMEs in the UAE strengthen their defenses and stay compliant.
Read More
Top 5 IT outsourcing companies in Dubai to enhance your business technology and efficiency.
Read More
Stay ahead with the top 20 cybersecurity trends shaping 2025, helping businesses prepare for emerging threats and technologies.
Read More
Stay ahead with the top 20 cybersecurity trends shaping 2025, helping businesses prepare for emerging threats and technologies.
Read More
Dubai businesses rely on Cisco routers for secure, reliable network connectivity, making them a top choice for enterprises and SMEs.
Read More
Cloud security is essential to protect data and ensure safe digital transformation.
Read More
Tips to select the best outsourcing partner for your business success.
Read More
Making IT budgeting easier and more effective for businesses.
Read More
Secure, unchangeable backup systems to protect critical data from loss or tampering.
Read More
Common network problems faced by businesses in Dubai and how to resolve them.
Read More
Comparing biometric and card-based access control methods for enhanced security.
Read More
Leading IT managed services in Dubai for seamless business operations.
Read More
Dependable network setup and support services in Dubai to keep your business connected.
Read More
IT budgeting is vital for SMBs to manage costs and enhance security.
Read More
A quick guide to must-have cybersecurity tools every Dubai-based business should use for stronger protection.
Read More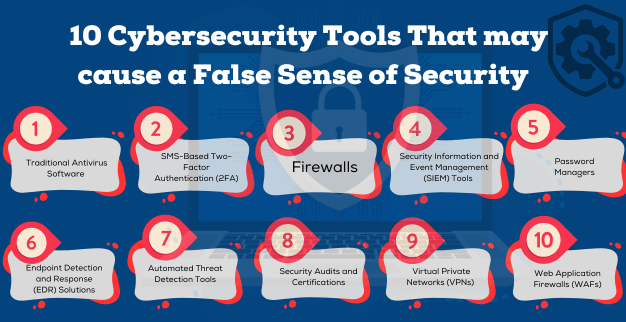
A look at popular cybersecurity tools that might give businesses a misleading sense of complete protection.
Read More
Explore how cybercriminals exploit QR codes and how businesses in Dubai can stay protected.
Read More
A quick checklist to help SMBs strengthen their cybersecurity posture and reduce risks.
Read More
A roundup of the most impactful cybersecurity breaches of 2024 and their business lessons.
Read More
Set clear cybersecurity goals to strengthen defenses and reduce risks in the new year.
Read More
Choosing between in-house and outsourced IT services impacts cost, control, and efficiency.
Read More
Log monitoring is key to ensuring security, compliance, and smooth operations.
Read More